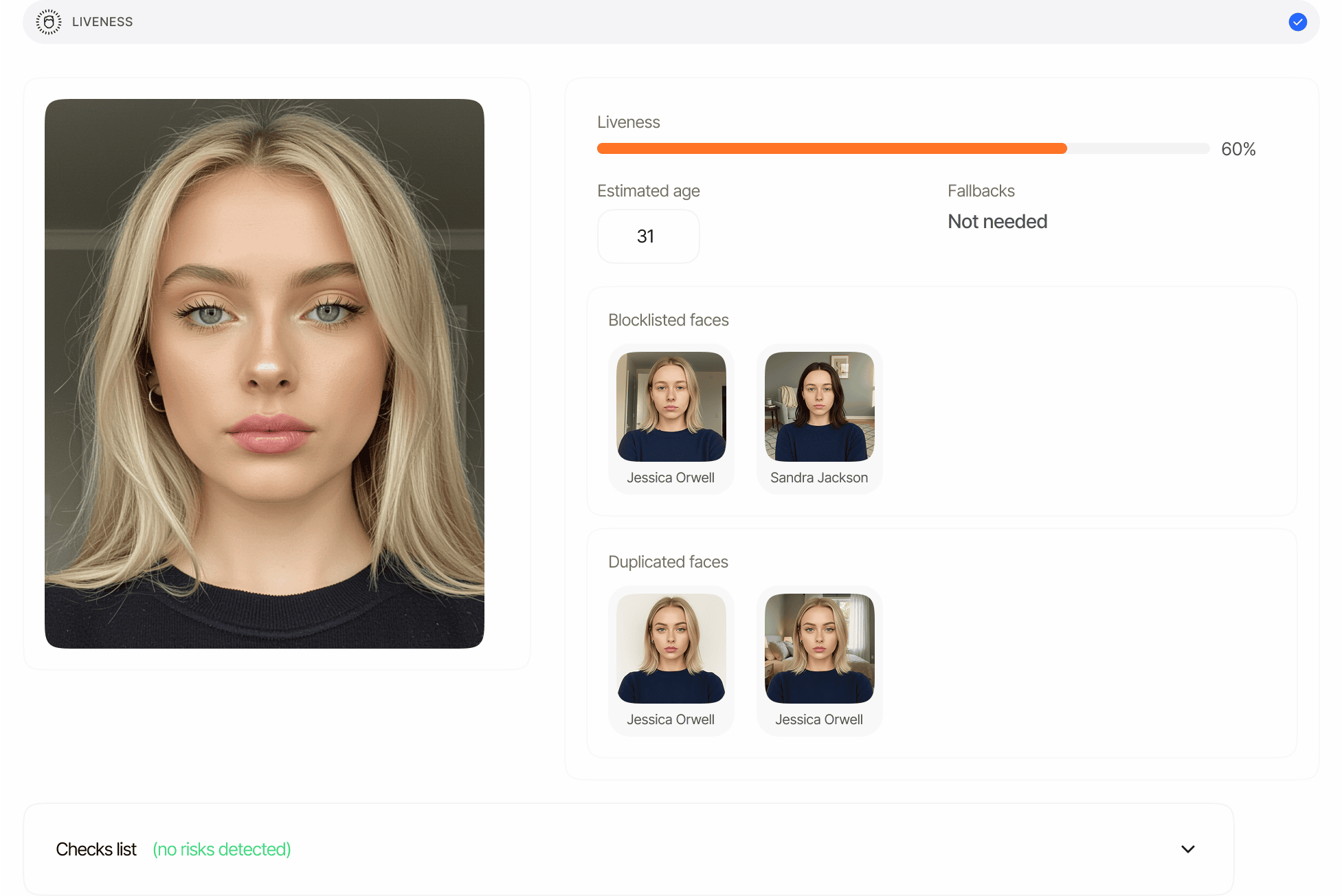
Automatic Face Search Integration
Face Search is automatically performed during liveness checks in verification sessions to detect duplicate users and check against blocklisted faces.
Automatic Duplicate Detection
When a user completes a liveness check during identity verification:- Their facial biometrics are automatically compared against all previously verified users
- The system identifies potential duplicate accounts based on facial similarity
- Matches are flagged according to your configured similarity thresholds
- You can review and take action on potential duplicate users
Blocklist Integration
Face Search seamlessly integrates with the blocklist feature:- During verification, faces are automatically checked against your blocklist
- If a match to a blocklisted face is found, the verification is automatically declined
- This prevents previously identified problematic users from creating new accounts
- Helps maintain the integrity of your verification process
API Access
Face Search functionality is also available through our API, allowing you to:- Programmatically submit face searches
- Integrate face matching capabilities into your own applications
- Build custom fraud detection workflows
- Create automated systems for duplicate detection
Key Features
- High Accuracy: Advanced biometric algorithms provide reliable match results
- Configurable Thresholds: Customize match sensitivity based on your risk tolerance
- Comprehensive Scanning: Search across all your verified users
- Rapid Results: Process searches quickly even with large user databases
- Privacy-Focused: All processing happens within your secure environment
Configurable Thresholds
You can customize search sensitivity by setting different thresholds for similarity scores:These thresholds can be adjusted based on your risk tolerance and security requirements.
How It Works
Face Extraction
When a search is initiated, the system processes the reference image:
| Process | Description |
|---|---|
| Feature extraction | Isolates facial features from the reference image |
| Normalization | Standardizes facial data for consistent comparison |
| Quality validation | Checks image quality and facial clarity |
| Vector encoding | Creates a mathematical vector representation of the face |
Comparison Algorithm
The system searches across your entire database of verified sessions:
- Compares the reference facial vector against all stored vectors
- Employs advanced neural network architecture optimized for speed and accuracy
- Supports two search modes: most similar (ranked list) and blocklisted or approved (status-filtered)
- Processes large databases rapidly using optimized indexing
Similarity Scoring
For each comparison, a similarity percentage is generated:
Your configured match thresholds determine which results are flagged.
| Score Range | Interpretation |
|---|---|
| 90%+ | Strong match — very likely the same person |
| 70–89% | Possible match — may require manual review |
| Below 70% | Likely different individuals |
Results Delivery
The system returns a comprehensive result set:
- Ranked list of potential matches sorted by similarity score
- Match details including session ID, verification date, and vendor data
- Similarity percentage for each match
- Match images available for visual review
- Blocklist status indicating if the matched face is blocklisted
Similarity Percentage
The similarity percentage is the core metric used to determine potential matches:- High percentage (typically 90% and above): Indicates a strong likelihood that the faces belong to the same person.
- Medium percentage (70-89%): Suggests possible matches that may require further review.
- Low percentage (below 70%): Likely indicates different individuals.
Use Cases
- Fraud Prevention: Identify users attempting to create multiple accounts
- Enhanced KYC: Add an additional layer of verification to your KYC process
- Regulatory Compliance: Meet requirements for detecting duplicate accounts
- Access Control: Verify user authenticity for high-security areas
- Law Enforcement: Assist authorized agencies in identifying persons of interest