How it works
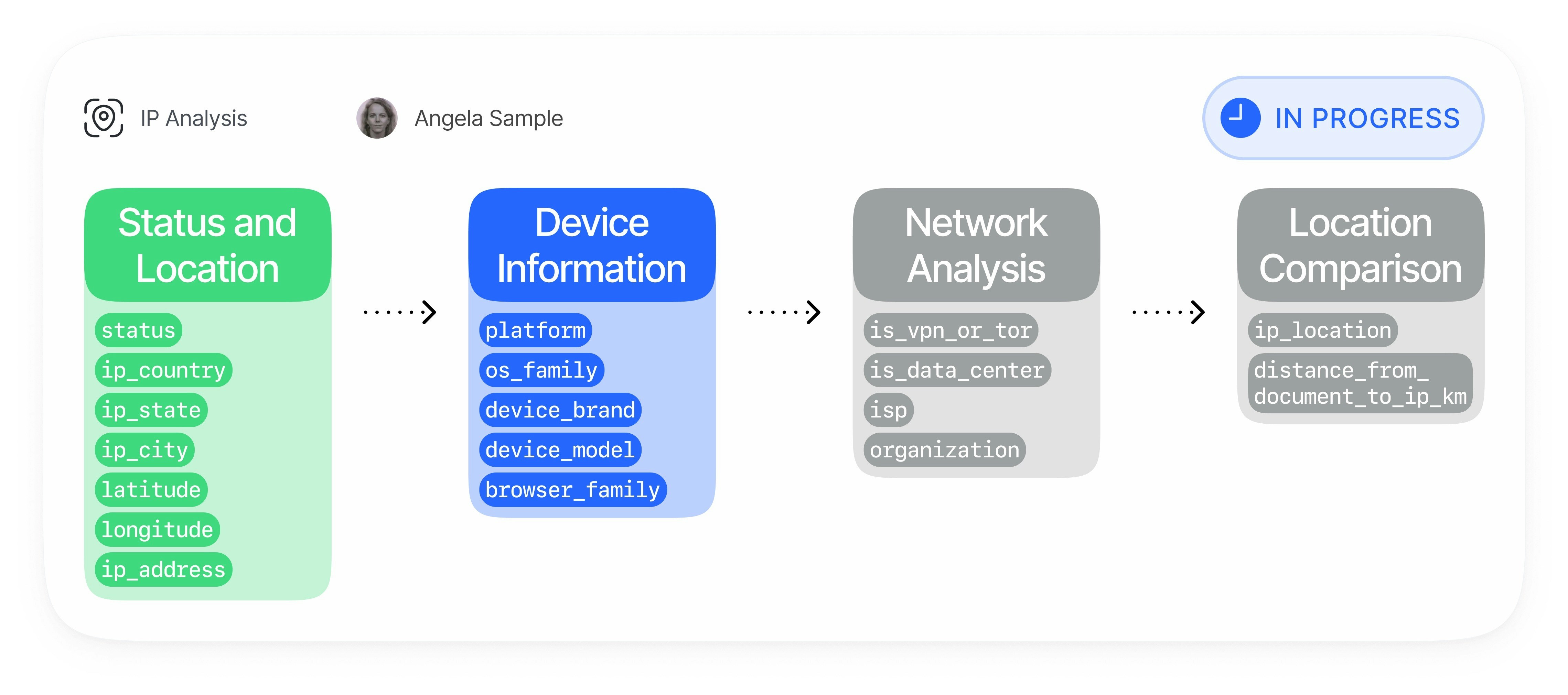
Our Advanced IP Analysis process delivers comprehensive location intelligence by analyzing user IP addresses and device information. This solution combines advanced geolocation technology, VPN detection, and cross-verification to provide reliable location verification at scale.IP Capture
The system securely captures key connection data during the verification process:
| Data Point | Description |
|---|---|
| IP Address | Automatically collected during verification without user action |
| Device Information | Browser type, operating system, and device details |
| Connection Details | Network protocols and connection characteristics |
Geolocation Analysis
Our advanced algorithms determine the user’s precise geographic location:
- High-precision IP location mapping
- Multi-source data verification for accuracy
- Geographic hierarchy extraction (country, region, city)
- Coordinate plotting for precise location identification
Risk Assessment
Our system performs extensive checks to identify potential threats:
| Check | Purpose |
|---|---|
| VPN & Proxy Detection | Identify masked connections |
| Tor Exit Node Identification | Detect Tor network usage |
| Data Center IP Recognition | Flag non-residential IP addresses |
| Historical IP Risk Analysis | Evaluate IP reputation over time |
| Suspicious Location Patterns | Detect anomalous geographic behavior |
Cross-Verification
Comprehensive validation against trusted reference points:
- Document address coordinates
- Expected location patterns
- Distance and direction calculation
Verification Features
Our IP Analysis service offers several key features to enhance your verification process:Precise Geolocation
- Accurate Location Data: Pinpoint the user’s location based on their IP address
- Detailed Information: Provide country, region, city, and approximate coordinates
- Protocol Support: Handle both IPv4 and IPv6 addresses
VPN and Proxy Detection
- Mask Detection: Identify if the user is accessing the service through a VPN or proxy
- Risk Flagging: Alert to potential attempts to hide true location
- Tor Exit Node Recognition: Detect if the user is accessing through the Tor network
Location Comparison
- Distance Calculation: Measure the distance between document address and IP location
- Direction Analysis: Determine the directional relationship between locations
- Risk Assessment: Flag suspicious discrepancies for review
Device Intelligence
- Hardware Identification: Collect device brand and model information
- Software Analysis: Identify browser family and operating system
- Platform Recognition: Differentiate between mobile and desktop connections